Cybersecurity Insights & Expert Guidance
Stay ahead of evolving threats with actionable cybersecurity insights, real-world case studies, and expert guidance from Inventive HQ's security team.
Featured Series

Python Data Types | Strings Numbers Collections
Master strings, numbers, collections, and datetime for effective programming
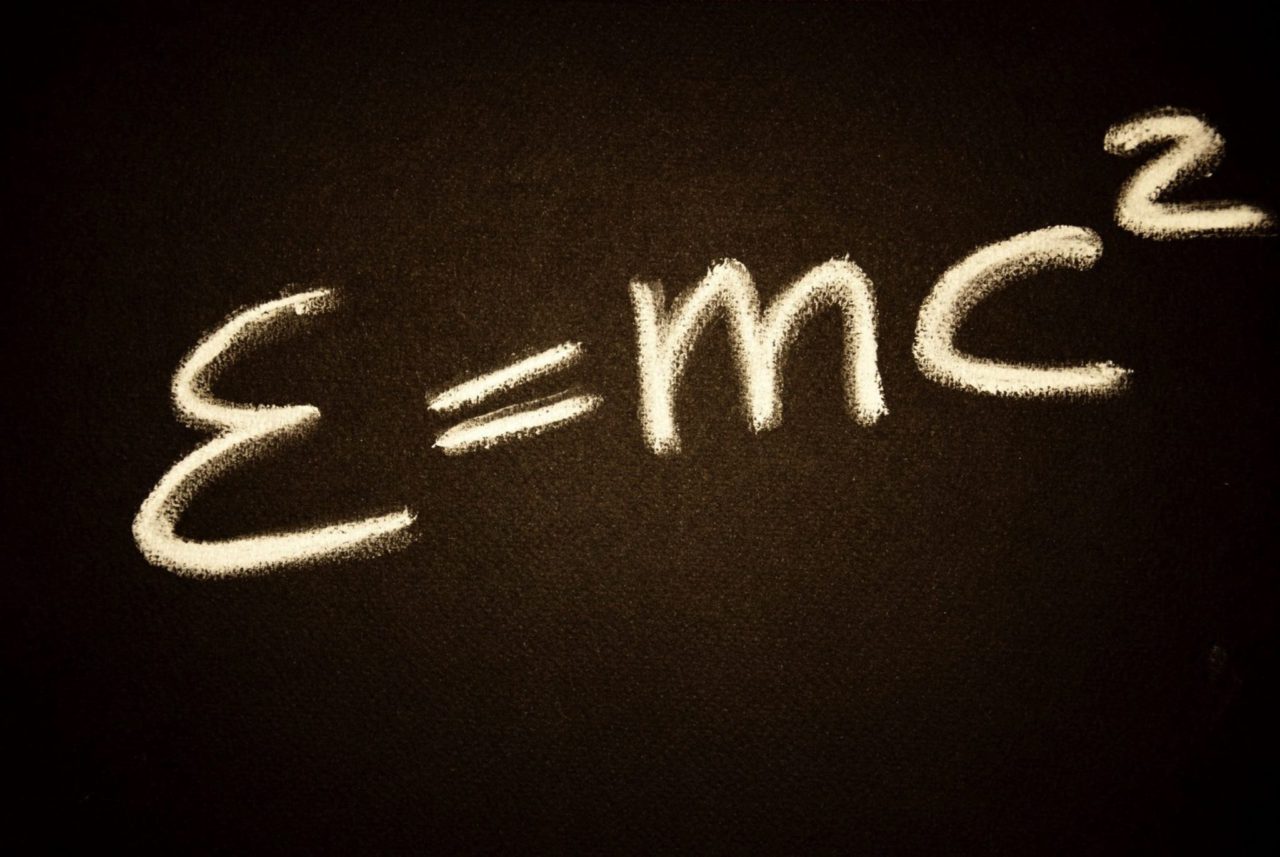
Python Math Operators | Complete Guide
Master addition, subtraction, multiplication, division, exponents, and more with clear examples

Vagrant with VMware vCenter Integration | Complete Setup & Configuration Guide
Set up Vagrant with VMware vCenter to provision and manage virtual machines effortlessly

Python Data Structures | XML JSON CSV YAML
Explore XML, JSON, CSV, YAML, and database structures with practical examples

Python Functions Guide | Create Reusable Code
Master creating reusable functions to boost code efficiency and improve programming skills
HTML Encoder/Decoder
Encode and decode HTML entities for safe display in web pages with special character handling

Hybrid Cloud Business Guide | Best of Both Worlds
Combine public and private clouds for optimal flexibility, scalability, and cost-efficiency in modern business

CISO vs vCISO: Which is Right for Your Business?
We compare in-house CISOs and virtual CISOs (vCISOs) to help you choose the right fit. Learn which option offers better security, flexibility, and ROI for your business.
Incident Response Services for Small & Medium Businesses
We help growing businesses prepare for cyber incidents, respond 10x faster when attacks happen, and meet compliance requirements—all without the overhead of hiring in-house.
Industry Specific Cybersecurity
We understand your industry’s unique challenges, compliance requirements, and cybersecurity risks — because we’ve been protecting businesses like yours for over a decade.

KVM Installation Guide | Linux Virtualization Setup
Master KVM virtualization with this comprehensive step-by-step installation and configuration guide for enterprise environments.

Cloud Security Assessment Results
Discover the hidden vulnerabilities that cause 95% of cloud security breaches—and how we find them

Java File Handling Guide | Modern I/O Techniques
Master Java file operations with comprehensive examples, best practices, and modern techniques for efficient data management
JSON Formatter & Validator
Format, validate, and beautify JSON with syntax highlighting, error detection, and tree view
Legal Cybersecurity
Navigate state bar regulations, protect attorney-client privilege, and build client trust with cybersecurity solutions designed specifically for law firms and legal service providers.
Page 12 of 64 • 959 articles total
Stay Ahead of Cyber Threats
Get expert cybersecurity insights, threat intelligence, and best practices to protect your business.