Cybersecurity Insights & Expert Guidance
Stay ahead of evolving threats with actionable cybersecurity insights, real-world case studies, and expert guidance from Inventive HQ's security team.
Featured Series
Color Picker & Converter: HEX, RGB, HSL Tool
Pick colors and convert between HEX, RGB, HSL, and HSV formats with visual picker and accessibility checker. Perfect for designers and developers.
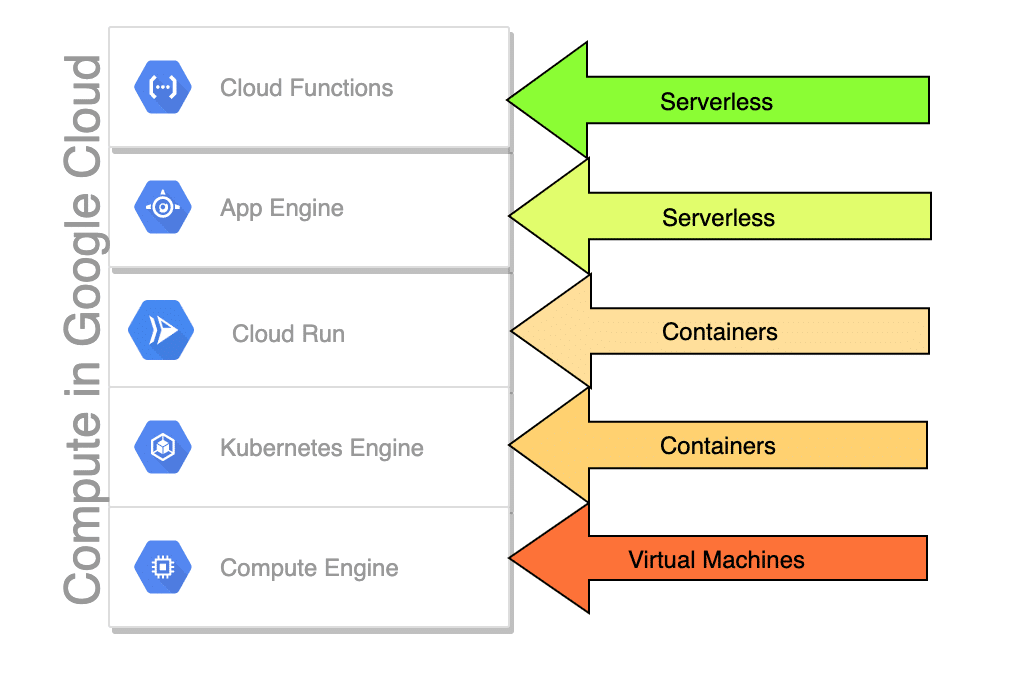
Comparing 5 Kinds of Compute on Google Cloud
When you think of compute, your mind probably goes straight to virtual machines. But there are actually at least 5 different kinds of compute on Google Cloud.
Best Container Orchestration Tools 2025 | Compare 73 Platforms
Discover the best container orchestration tools for 2025. Compare Kubernetes, Docker Swarm, AWS ECS, and 70 more platforms. Find the perfect solution for deployment automation, enterprise workloads, and IoT/edge computing.

Log Files Guide | Complete Management & Security Tips
Master log file management for enhanced cybersecurity monitoring, troubleshooting, and compliance. Learn types, formats, and best practices for effective log analysis.

Complete OpenFiler Configuration Tutorial
Master LDAP setup, user management, network ACLs, volumes, and iSCSI LUN configuration for enterprise storage solutions
SMB Compliance Challenges | Cybersecurity
Compliance is entirely achievable for SMBs when they choose the right approach. Discover practical solutions that balance cost, effectiveness, and sustainability for your specific regulatory requireme...

iSCSI NFS CIFS Storage Protocols | Master Enterprise Connectivity
Master storage connectivity protocols with our comprehensive guide. Learn iSCSI, NFS, and SMB/CIFS configuration for Windows and Linux environments to optimize your enterprise storage infrastructure.

Convert JSON to CSV in Python: Complete Tutorial
When working with data in Python, you’ll frequently encounter situations where you need to convert between JSON and CSV formats. Whether you’re processing API responses, preparing data for analysis, o...

JSON to CSV Python Converter | Transform and Export Data with Code
Learn how to seamlessly convert between JSON and CSV formats using Python, with comprehensive examples, error handling, and production-ready code.

Building REST APIs with Flask: Complete Python Guide
Learn to build dynamic web applications with Python and Flask – from installation to deployment with step-by-step tutorials
Cron Expression Builder: Schedule Jobs Easily
Build and test cron expressions with visual scheduler, human-readable descriptions, and next run time calculations
CrowdStrike MDR: 24/7 Business Protection
At 2:47 AM on a Saturday morning, alarms began flashing in InventiveHQ’s Security Operations Center. CrowdStrike’s AI-powered detection engine had identified suspicious PowerShell activity on a health...

CrowdStrike vs Arctic Wolf 2025: Platform vs Service MDR Comparison
Technology platform vs service partnership: Compare CrowdStrike’s comprehensive endpoint platform with Arctic Wolf’s human-led security operations for SMBs

CrowdStrike vs Cylance: Which Endpoint Security is Best in 2025?
Compare CrowdStrike’s comprehensive platform vs Cylance’s AI-powered execution protection for small business endpoint security

CrowdStrike or Huntress? SMB Cybersecurity Platform Guide 2025
Small and medium businesses face 70% of all ransomware attacks. Compare CrowdStrike’s complete security platform replacement vs. Huntress + Windows Defender’s layered defense approach.
Page 8 of 64 • 959 articles total
Stay Ahead of Cyber Threats
Get expert cybersecurity insights, threat intelligence, and best practices to protect your business.